
by Dr. William Sen
digitalwelt-Columnis for Computer Security and Information Law



Today I will talk about how the scam baiter Jim Browning gains access to the scammer’s network. Because that’s the one question he seems to avoid in his videos, I will reveal the hacking technique he is using.
This is also a good opportunity to understand how scam baiting works overall.
If you haven’t heard of Jim Browning — he is not revealing his real name — he is a YouTuber who spends a good amount of time and effort to hack into the network of scammers — mostly located in India. If you are not familiar with him, I recommend starting with this video below:
Watching videos of him, you will hear him say many times that when those scam baiters try to ‘scam him’, he would ‘reverse this connection and gain access to the scammer’s PC’. Of course, as a computer scientist, I know that there is no such thing as ‘reversing a connection’ per se, unless of course you take it more as a figure of speech. Fact is, you can’t just hack into somebody’s computer just because he has gained remote access to yours through a remote control software such as TeamViewer, GoToMeeting, Zoho Assist or similar. Because that’s the kind of software the scammers use.
What’s the Magic Behind Jim Browning’s Hacking?
What he is most likely doing is what we call delivering a ‘payload’. A payload is a computer executable file such as an .exe file. That’s exactly what Jim Browning is doing to the scammers.
To make a hack possible, Jim Browning is using a RAT software. RAT is the acronym for Remote Access Trojan: A RAT comes usually with two pieces. The software itself allows the hacker to control the victim’s computer — often known as the RAT client. Then there is the payload: Once the other person starts the payload (the exe file), that computer will establish a connection to the hacker’s RAT client; thus, giving the hacker full access to the infested computer. Many well-engineered RAT tools will even come in three pieces:
1) RAT Proxy
This is the software piece the hacker installs on a server somewhere, usually on a Linux based server, either a dedicated or cloud based server anywhere.
2) RAT Payload
The RAT payload is the trojan horse file the victim has to run by being misled. Once that file is started on a Windows PC for example, it immediately puts itself into the white list of any installed antivirus and firewall tools, and hides itself from being detected through common tools such as Windows Services and similar. Often the tool will compromise core system files of Windows, so it acts like a normal Windows service where it then becomes extremely difficult to be identified as a trojan horse. And then it connects to the RAT Proxy.
3) RAT Agent or RAT Client
This is the dashboard the hacker has installed on his own Windows PC from where he has full control of the infested computer. The RAT Agent allows following options to the hacker among others:
- Manipulating the web cam drivers that will allow him to turn on the web cam covertly.
- Tab into the microphone and speaker to eavesdrop any conversation.
- Monitor every movement on the screen of the victim including mouse movements in real-time and the ability to capture screen as images or videos.
- Keylog everything that is being typed into the keyboard.
- Explore and download files on the victim’s computer covertly without the victim noticing.
- Install and manipulate software.
- Disable and activate any kind of settings including security settings and firewalls.
- Access to the computer’s network such as printers, and other locally or externally connected networks.
- Start, close and make use of existing software and processes.
- Make changes on the registry, services, make uploads, and run scripts.
The possibilities are endless. There is a vast amount of RAT software provided by hackers. Popular tools are СrunсhRАΤ, Vаynе-RаΤ, Pоwеrѕhеll-RАΤ, ThundеrЅhеll, Χееxе, and many more. Besides the popular hacking tools such as these mentioned above, governments are known to use more sophisticated and user-friendly RATs such as FіnFіѕhеr — which also can be downloaded if one has access for example to some underground sites used by the hacking scene.
Note: If you’re searching the RAT tools and company names mentioned in this article, don’t copy paste them into a search engine as you won’t find anything. I have made them unsearchable (it’s a simple grey hat technique). You have to type it into search engines manually if you want to see some results.
Below is a screenshot of АhΜyth Аndrоіd RАΤ — a RAT that allows hackers to control Android phones of their victims. You can see below in this case how the hacker has been notified by the RAT client that his victim has just started the payload (in this case an .APK file), and that the hacker now has full control over the victim’s smartphone:
The hacker now can activate the smartphone’s cameras, access files, listen to everything being spoken through microphone access, send SMS and read existing ones, see contacts and phone logs, and many more.
This is how FіnFіѕhеr is being distributed mostly in the darknet:
And it comes with a good number of documents and trainings which will tell you how to install and run it, and how to deliver the payload to the victim’s computer:

You can see above that FіnFіѕhеr seem to provide payloads through different devices, even through websites, and USB devices. This suggests that FіnFіѕhеr’s trojan horse or payload will most likely try to install itself on the victim’s computer when inserting a USB drive or visiting a certain website.
Looking at the FіnFіѕhеr software, I understand that you could be able to create your own EXE-files through an infection tool provided by FіnFіѕhеr. It looks like it basically allows you to create your own payloads. Because I can also see that you can select “will not trigger UAC prompt” on the software’s screen. I did not provide screenshots of the software since I would assume the developer behind FіnFіѕhеr called ‘Lеnсh ΙΤ ЅоІutіоnѕ’ could try to legally stop me from displaying their software’s dashboard by arguing its copyrighted media content. But you get the point.
But let me put it that way. If somebody were to look for these tools long enough and with perseverance, they would be eventually able to find them. Knowing where to look, it took me as a journalist not more than 15 minutes to find FіnFіѕhеr as you can see above.
Another way is if the scam baiter would code his own RAT tool which doesn’t have to be that sophisticated as it would have to fulfill only a couple items the scam baiter wants. Since the scam baiter would not have to deal with fancy dashboards, a simple script with a couple control items would suffice.
Now, with tools like this, Jim Browning can easily access somebody else’s computer, in this case the scammer’s PC. Now that we know what kind of tools Jim Browning uses to infest and control the scammer’s computer, the one question remains: How is he dropping the payload (the exe file) on the scammer’s PC?
Sniffing the Scammers Connection
Let’s have a quick intermezzo: First of all, without using any RAT tool, Jim Browning can trace back the connection using different tools known as ‘Packet Sniffers’ or ‘Network Monitoring Tools’.
There are plenty out there, and one of the popular ones is Wireshark. For example, I use Wireshark to trace VPN tools to see if they are in fact using an encryption when I’m testing VPN tools. These tools will also reveal the IP Address of other people gaining access to your computer — such as the scammer’s IP Address using a remote software.
Having the IP address of the scammer is useful in many ways. The hacker can trace their IP using several online tools called “IP Tracers” to see what kind of Internet Service Provider the scammer is using and where he is located at — assuming of course he is not using a VPN software to disguise his identity. Jim Browning shows on many videos that he was able to successfully trace the IP of his scammers back to them, so we can assume that the scammers are not very clever when it comes to obfuscating their identities through VPNs.
Having to know somebody’s IP will open a good pathway for further investigations. But there is not much else you can do with that information: You won’t be able to hack into somebody’s computer just because you have traced their IP.
Sure, you can try to find some open ports and give it a shot based on luck — but this isn’t the 90s anymore where you can easily hack through some open ports. It’s 2025 — and firewalls, operating systems and router securities have quite evolved since then.
A hack is a creative approach, custom designed to specific situations. And the best way in this case to hack to the scammer’s computer is if that person installs and starts a file you want them to start — the RAT method.
Delivering a Payload to the Scammer’s Computer
Let’s talk about the opportunity that arises when a scammer tries to scam you, and how a vigilante hacker such as Jim Browning can use this to his advantage to deliver the payload.
This is the most fun part because it involves creativity, and it’s a custom designed method that works perfectly with scammers.
A scammer usually gains access to your computer using a remote software tool once the victim allows it, thinking the scammer is a legitimate IT support guy trying to help. TeamViewer is one of the most popular tools, but there are many other tools such as Zoho Assist, RemotePC, and even Microsoft’s own remote tool.
Since Jim Browning knows the scammer is looking for files and access passwords that involves money, he will deliberately allow the scammer to access his computer which he has specifically prepared as a bait. Once the scammer gains access to it, there are a couple things Jim Browning can do. And the possibilities here are endless, based on your originality how you want to lay a snare.
But before he gets to that, he will do a little bit sniffing.
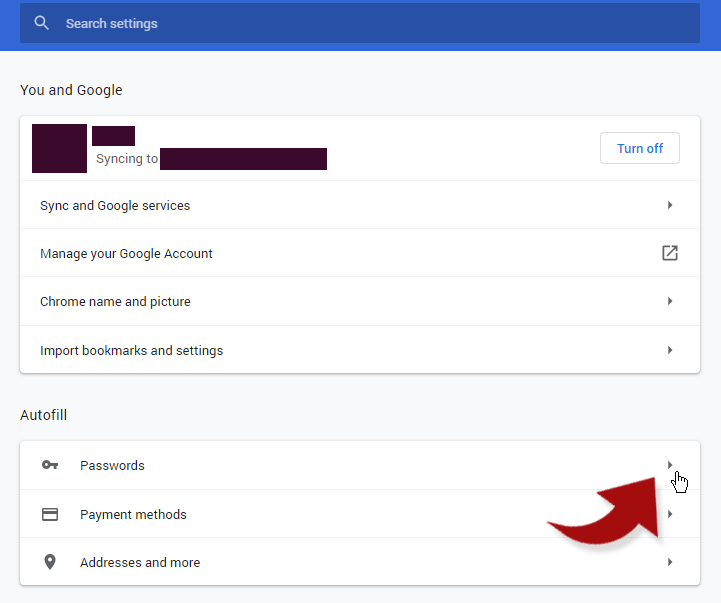
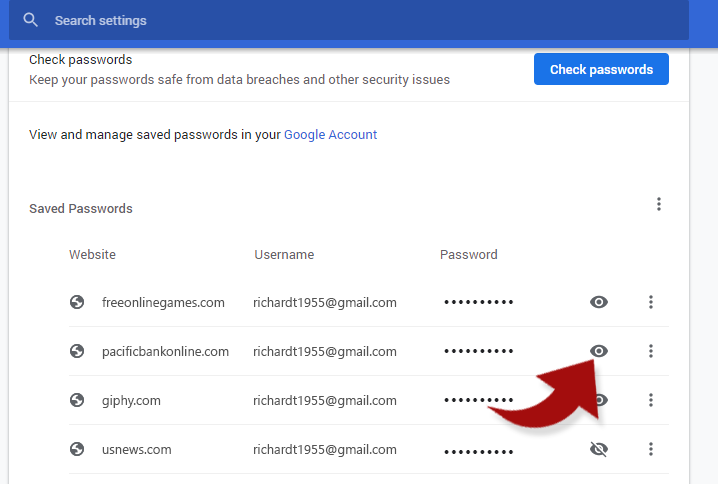
As Jim Browning demonstrates in his videos, the first goal of the scammers is to gain to your list of passwords stored in your chrome browser — that’s where all your auto filled passwords are stored. In your browser settings, you can access those stored passwords and actually see all the passwords with one click:
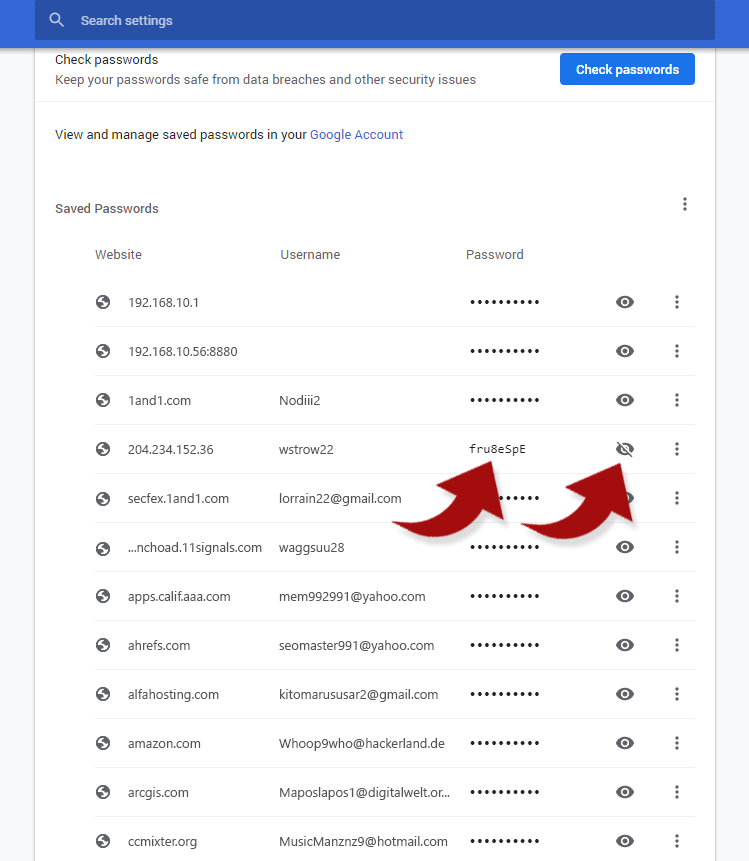
And once the scammer clicks on one of these, he sees all your passwords just like that:
Jim Browning also teaches us that the scammer favors remote software that allows them to black the screen of their victims, so the victim doesn’t see what the scammer is doing on the victim’s computer — as in stealing their passwords.
Since the accounts of the victims have lots of passwords stored, and at the same time the patience of the victim is limited, the scammer must act fast. He most likely won’t steal your password to your favorite radio streaming, but rather look for websites with monetary values such as bank accounts, payment hubs like PayPal, or online shops such as Amazon or Apple Store where he can purchase gift cards using your credit card credentials that are stored in those websites.
Method #1: Baiting Scammer With A File From Your Computer
This is the simple way. The scam baiter just leaves a file on his own computer, e.g. on his desktop, that says something as in “mypasswords.docx”.
A known tool called FakeImageExploiter will allows the scam baiter to turn his Window .exe files into a .docx file. It is basically the same as creating a mypasswords.docx.exe, however without the .exe being shown on Windows. Github.com/r00t-3xp10it/FakeImageExploiter explains this method pretty well.
The scammer will see this file on the scam baiter’s computer and download it. When he opens it, the payload will be delivered, and the scam baiter will now has full access.
Method #2: Baiting the Scammer With A Fake Bank
This is the least suspicious method and promises a much greater success rate.
Lesson number one: If Jim Browning were to bait the scammer with a valuable website such as a bank account, they will most likely try to steal that password first. Naturally, a scam baiter like Jim Browning would prepare his chrome browser with one valuable website such as of a bank, and the rest would be only there for smoke and mirrors like the image below. The scammer wouldn’t lose any time and immediately click on that bank account.
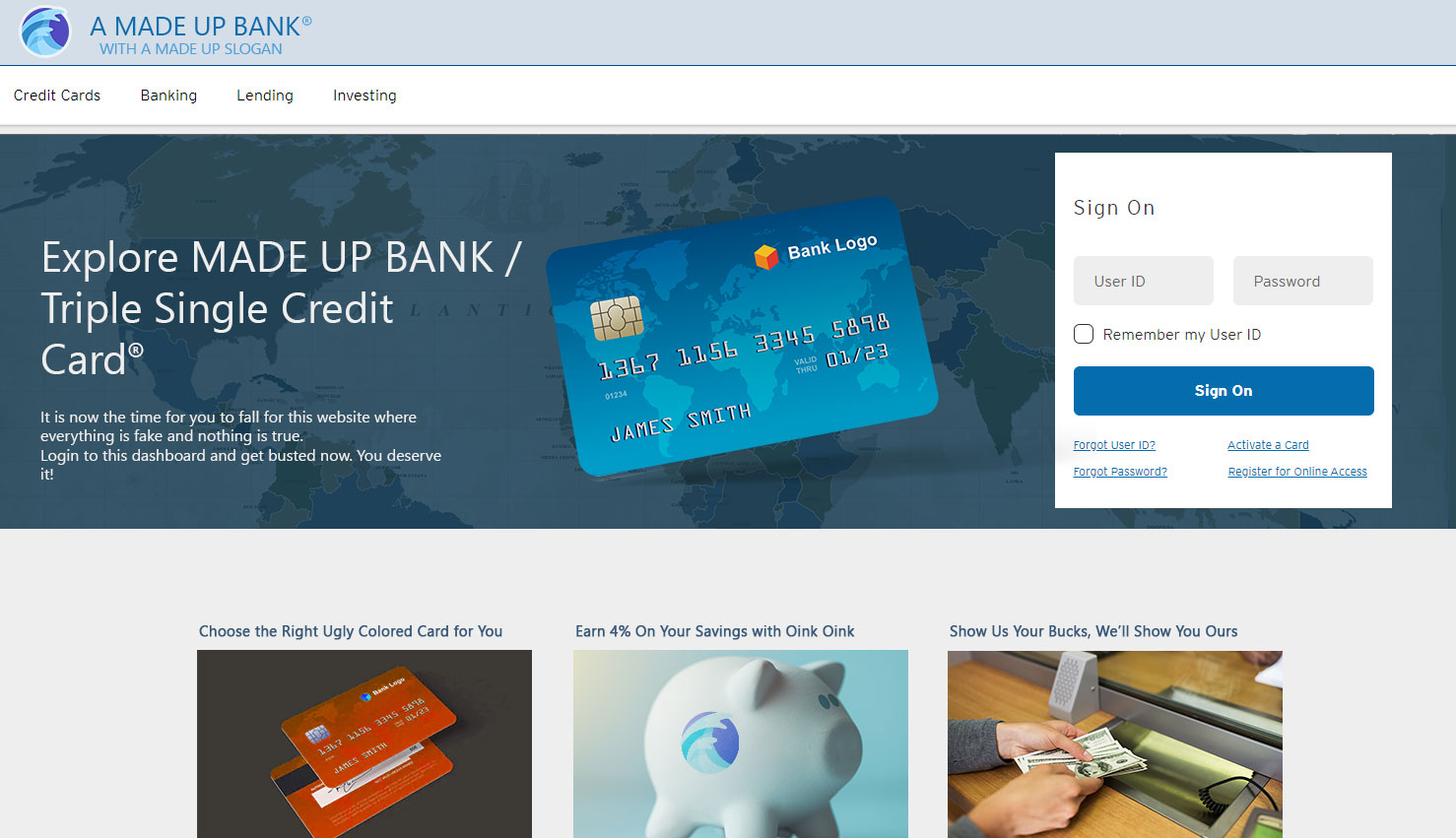
Of course, people such as Jim Browning would most likely use a free and bogus domain that sounds like a bank, e. g. pacificbankonline.com or whatever sounds somewhat legitimate.
Watching Jim Browning’s videos closely you will also realize that these scammers are not the brightest. I would guess that most of them are simple minded. You can assume that they don’t know much or anything about the U.S. or even world’s financial industry.
In many videos you can clearly see that even they tend to claim they are from San Jose, they are not even able to name one restaurant in that city. This brings us to the conclusion that they do not do any research or brain work altogether, nor are much prepared, but simply follow a monotonous process, and the only goal is to get money from the victim without further ado.
That actually makes the scammer an easy target, and baiting him to visit a website the scam baiter has created seems to be quite a good idea as long as it sounds like there is money involved — like the domain “pacificbankonline.com” I just made up as an example.
The scammer will immediately open that website of the scam baiter he just obtained from his victim’s browser; thinking it’s a real bank his victim has an account at. The scam baiter at the same time makes sure he has already created a website that looks like a professional bank. Here is one for you I just created for this article to illustrate how easy it is actually to create a design:
Platforms such as WordPress allow easy and quick setups of that kind if you are a skilled and experienced programmer with HTML and CSS capabilities. A hacker like Jim Browning is usually that kind of a person.
The scam baiter will probably want to make up a nice name for the phony bank. As a slogan he even might want to use something like “A J.P. MORGAN COMPANY” or “CITIBANK GROUP” just to make the phony bank look like a subsidiary of a more serious and bigger bank.
When the scammer visits that website, he will only login with the user ID and password without being distracted about anything else happening on that phony bank website. He sure won’t try to educate himself by reading any of the blog posts on the website. But if he does, the website would simply show a popup of a login window.
You can see clearly on Jim Browning’s many videos that once the scammer logs in to the bank account or payment website of the victim, the first thing the scammer does is to transfer and steal money from that bank to a predetermined recipient.
Now the scammer is about to download a little software that has been prepared for him to start: a hazardous .exe file that will compromise his computer. However, in order to make that happen, the scammer needs to be provided with a good reason to do so. Now, the vast creativity and social engineering skills of the scam baiter who is also a hacker with years of experience comes into play.
We already know that the first thing a scammer does after logging to the bank account is to click on the ‘wire transfer’ to steal money.
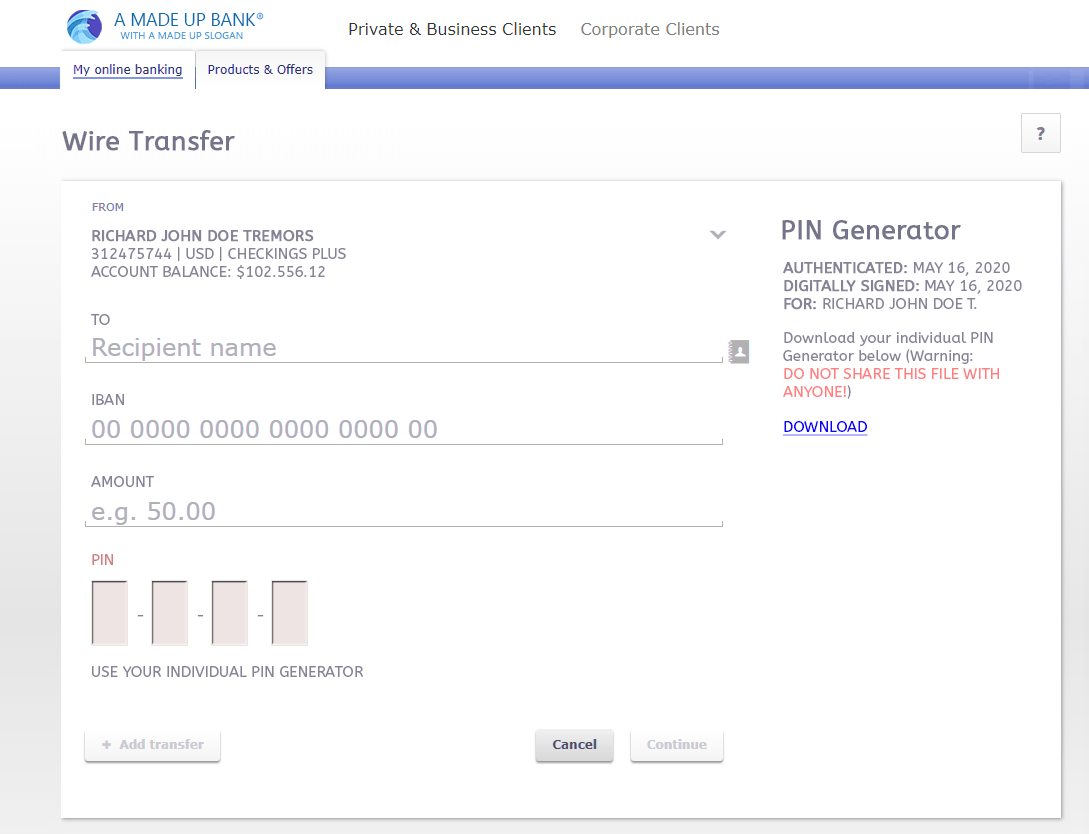
The easiest way would be to provide a small download tool on the wire transfer dashboard such as a bogus ‘PIN Generator’. The scammer will think that he needs to start this tool in order to create a PIN that’s needed to complete a wire transfer.
Below is a good way to trick the scammer into downloading the so-called ‘PIN Generator’. On the image below I made it look like a PIN Generator that has been already authenticated and digitally signed by the bank account owner — which just makes it look more legitimate — but in fact is just another way of creating smoke and mirrors; one of the many social engineering hacking methods.
The scammer will immediately fill out this form and try to send money to someone. And will download the PIN Generator which can be a file such as “PIN-GEN-JohnDoe4455.exe”. If you want to put more obscurity to it you could even ask for a SMS conformation before the download at which the scammer will ask the victim to open his phone and provide him that number. This will take away the suspicion of the scammer even more thinking that it wasn’t too easy to transfer money. More reason for the scammer to download the .exe file.
Once the .exe file is downloaded and executed on the scammer’s PC, he would have installed the scam baiters trojan.
A good payload is usually embedded to another .exe file that actually can have a real purpose and features. For instance, the .exe file would indeed open a fake PIN Generator tool but only to ask for another SMS confirmation code. That way the scammer would not be suspicious, and once again has to ask his victim to look at his phone for a text message. Since the payload has been delivered successfully, that now allows the scam baiter to find his way out of this session with a good exit strategy.
Exit Strategy
Before the scam baiter baits the scammer, he has an exit strategy already planned out. Once the scammer has installed the payload and the scam baiter now has gained access to his PC, it will be crucial for the baiter to come out clean and not to arouse suspicions that could lead the scammer to investigate. The scam baiter will therefore give the scammer something he is most likely to receive all day long: mistrust. The goal is to let the scammer believe that his attempt has failed, which probably will happen 99% of the time, and he will then move on to the next victim. That’s one way to do it:
The scammer needs an explanation why the .exe file he has opened didn’t lead to his intended goal. Therefore, the payload has to provide a feasible explanation.
In the case of the fake PIN Generator this can be easily done when the tool (payload) asks for a task the scammer can’t complete — such as to activate the tool with another PIN that would be needed through a text message.
In the example above the scammer now will try to obtain the SMS text message from his victim’s phone: “Sir, you should have received a text message. Can you provide me that number”. Now it’s time for the victim (scam baiter) to break up the relationship.
Hackers such as Jim Browning plan their exist strategy well. You can see this on his videos how well he is structured by collecting and organizing all the information he is gathering during his calls with the scammers.
The scammer now should be told by the scam baiter something as in: “This is a PIN from my bank. Are you trying to steal my money from my bank”? That’s a good way to end a call by switching the role to a disappointed customer who now has lost his trust. What better reason to end a call? While the scammer now will most likely try to calm him down, the scam baiter’s website will have already logged the scammer out by displaying this message:
“Only one user section is allowed. Another user is already logged into this account. This user must log off this machine before you can log on.”
At the same time, the scam baiter will now change the password to his phony online bank, thus making it impossible for the scammer to see the dashboard again.
Once the scammer clicks the close button on the payload, the scam baiter, who already has full access, now can easily overwrite the payload .exe file with something inconspicuous such as a bogus update application, or just close it and delete it himself.
And while all that happens, the scam baiter will engage the scammer with accusation talks to drive his attention from what is just happening. Eventually the scammer will end the call himself realizing his attempt failed by saying things such as ‘I can’t help you, sir, you have wasted much of my time’.
At this moment Jim Browning would have full access to the scammer’s PC, and the scammer would have hung up on him telling himself: ‘Up to the next one’.
In a sense, you could say that Jim Browning is actually ‘reversing the connection’, if by connection you mean the social aspect of the conduct. Because that’s exactly what Jim Browning is doing: He is using the same methods the scammer uses, but in reverse.
Note
I have to write this to protect myself, sorry guys: All these explanations are opinions and assumptions. I never talked to Jim Browning personally and he never explained to me how he does it, and as far as I know I’m using ‘Jim Browning’ as an anecdote for any scam baiter. Do not to install any RAT, do not to try to bait scammers with any of these methods described as they might get you in trouble. Do not download nor install FіnFіѕhеr or any of the tools mentioned above if you do not have the proper license. And by the way, just in case: I never said I downloaded nor installed FіnFіѕhеr, did I? In a sense I do not know about anything I’m writing here and it’s just a figment of my imagination. Legal Notice OFF.



by Dr. William Sen
digitalwelt-Columnis for Computer Security and Information Law



Dr. William Sen has been a computer expert for over 25 years. He has published numerous books and articles in the field of network security and hacker culture, including for TV and radio. William lives in San Diego, California.








I was able to see every message, pictures and videos on my ex’s phone with the help of this amazing hacker Alberto. I was about to make the biggest mistake of getting married to him but after reading his chats I discovered he had already been married in another country with 2 kids. This really broke my heart but I am very happy I did not end up in that marriage. All thanks to Alberto for helping me see the truth. If you need help catching a cheating partner, Contact Zattechhacker AT gmail, c0m
Excellent article, very informative. Pity the hate responses but that is the sad world we live in. Now we are all in agreement that greed drives the scammers, but what of the scam baiters? They too seek fame and fortune, it’s quite amusing to see their monetized YouTube channels, today’s youth get much of their kicks watching their YouTube heroes “performing” especially in live sessions. Make no mistake, scam baiters may have begun their YT careers with good intent but soon “evolve” themselves. And their lazy stereotyping of scammers is disturbing in their racist overtones.
I assume, that you might be aware.. but:
Such articles that “teach” scammer how to AVOID certain tricks, are rather destructive to the cause of scambaiting and getting rid of them.
Sure it’s fun to talk about all the tools and things, but actually providing a very effective trick to bait them too!?
I would very much like for you to reduce that part of your article to a more vague minimum to not educate any more scammers on what to look out for and try to avoid.
Vague like: “and then have SOMETHING on your bank, that enables the hacker to deliver the payload”
The skilled hacker as you mentioned, should be imaginative enough to come up with a solution on their own. And if not, maybe consider not to scam bait, lacking the social engineering part.
And I would def. add a “What now, that he has a connection?” “How to actually try and stop them?”
There are several ways, lurk and watch for payment gateways to shut down, Banks (mules) to report and close, Giftcards to intercept and block/flag, try to reverse Payments to refund victims.. etc.
Reporting to officials, police or the community for further assistance (e.g. scammer.info)
Hope you find it in you to think about this and help us (the scam baiting community) out by not exposing tricks and things to actually look out for.
Jim Browning show only successful hacked computer but failed hacked computer are not exposed in his channel
Not all scammaers are silly ,some of them are professionals and well educated.
what you are told about RAT and trojens is not a good idea because scammer is not a child to click on the files or go to website to try passwords for more reasons
1)His goal is downloading the maximum he has his tool to wipe and search sensitive data
2)All RAT and trojens are known by anti virus ,even if it is modified or crypted but the main definition is known and is is hard to bypass security
I think that Jim Browing can’t do that with windows but he use Linux in the background to bypass security.
did a failed scammer write this?
Dear William
I came back to your article, but I cannot do it. It’s not my field. Really appreciate if you can suggest someone to infiltrate a RAT into my scammers hiding in Telegram. Regards.
Dear Dr William Sen
Thanks for your article. I was also victim of scammers a couple of months back. They are still active. Wish you could recommend somebody to trace and disrupt them. I cannot do code at that level.
Regards.
“HAHA”, You know almost all of what you are talking about. You should learn that buffer overflows are from executables-the exact same thing as installing RATs as described. You can’t have a buffer overflow without executing a program. Why do it the hard way when a PS script does the trick?
To help you learn more: invicti.com/blog/web-security/buffer-overflow-attacks/
And if you can’t find anything constructive to say, shut up. You hurt the cause and the work when you criticize the work.
And you think you’re smart enough to pull a stupid stunt and try calling a real engineer out… lol.
Nice write up. Leaving some juicy .exe on the desktop as a honey pot is probably the easiest way. Scammers are greedy and will always go after low hanging fruit like this. I dont think you can “reverse connections” on things like team viewer and anyconnect, that would be a massive security flaw on those legitimate remote applications.
I once hacked some forex scammer but did it differently. I went to their “trading website” and found an XSS vulnerability, I added some malicious javascript and when the scammers viewed it i got their admin credentials (cookie) and I could log into their account. From their i could see all the other victims that had deposited money into the “trading account” :)
Even if there is a difference in the work of jim brawining in catching fraudsters, but the two methods that have been explained are very possible to apply in reality
Social engineering methods and tricks remain the best way for the hacker to his target, but how to do the trick and make the target convinced to download an executable file is the most innovative and difficult…
The post is beautiful and informative…thank you:)
Great article. Thanks. BUT, you need an editor.
This is not what they do. Typically they use a buffer overflow, in a kind of man in the middle attack since the computer they are connected to is a virtual machine.
Jim browning is a software engineer, and likely he has created software that easily does this that he has given this software to other scam baiters like perogie. All of the scam baiters communicate to each other, and help each other out. They are all friends at this point.
Yeah, you could use a RAT, but getting that RAT on the scammers machine… The scammers don’t download anything and run it on their machines.
But I know for a fact what they do and it is not a RAT. They are truely reversing the connection with a buffer overflow, which allows them to use anydesk to look at the scammers files. this is clear because once the scammer disconnects anydesk, the scam baiters have no more access to the machine.
Now Jim browning likely installs RAT’s in the machines that will allow him to continue to spy. He most likely writes them him self to avoid detection. But he would have to go in first through anydesk reversed connection and allow the RAT in the soft firewall on windows.
You call your self a software security person … l0l.
Nice try scammer.
Brilliant, thanks for the overview.
I think it should be underlined that in some jurisdictions, if you’re running anything on the scammer’s computer it is consider *worse* crime than what the scammers are trying to do using social engineering on your computer. At least here in Finland, I wouldn’t try acquiring remote connection to scammer’s computer without the scammer’s consent. The law was designed to prevent vigilante activity so you have to contact the police every time instead. For other countries, it might be different. I’ve been told that in some countries you cannot trust the police and it would be a shame to live in such a country.
However, passive methods that do not require running code on the scammer’s computer are okay. For example, using social engineering to get the scammer to access a web site that then collects IP address, OS version info, screen resolution and other details that browsers leak automatically is considered okay, especially when the scammer follows a link or types the domain by himself or herself.
There is the law and there is common sense. In some countries such as the United States for example, both subjects fall under the same type of understanding. Legally it might be a ‘crime’ to hack in somebody’s computer. If you however do this to expose somebody’s else’s immoral actions, there would be no court nor jury that would prosecute you as it would not make any sense. So, Jim Browning’s actions would not be considered in any way criminal in the U.S.
In many modern law, such as in many European countries, crime is defined as something when somebody harms another and gains an advantage in the process. Since Jim Browning is not harming anybody, and his motive is not to take advantage of somebody, his actions would not be considered to be a crime. Preventing a crime and exposing a criminal act cannot be considered a crime.
On the contrary, Jim Browning would be more likely to be asked by U.S. government organizations to help them out. While he would get incentives in one country, he would be punished in Finland? That would be a shame I think for countries such as Finland. I find this hard to believe, but then again I am not familiar with Finnish law. Do you have any law texts that you can refer to? Thanks.
This is correct.
I read the incredible article by “Jim Browning” and other contributors regarding scamming. I was scammed a few months ago. It was a situation which was not addressed in the article. I dialed a legitimate number to inquire if my check was received. The person who answered the telephone was exactly how you described the scammers. The conversation went on for quite a long time. I should have hung up. It was my fault, and I know better, but they “got me” ! Fortunately, I was only out $200.00 but the feelings of shame and guilt were immeasurable. I was advised that the scammers sometimes are able to hack into legitimate numbers. I called the number the next day, it was to Pay Pal, and a representative answered. Learned a bitter lesson! Thank you again.
I believe that you don’t have enough creativity.
This may have worked in the first tries, but with Jim Browning becoming so popular and infamous to these scammers, they will see it coming miles away. They will be careful to not download anything and execute it, ever.
And yet Jim Browning is still hacking these guys like crazy, so there must be another explanation.
Either Jim is using a drive-by exploit, or he found out a 0day in the RATs these scammers are using (I would be fascinated if this last one is a possible vector)
If 0days are exploited, these scammers would have zero chance to protect themselves as it is a skill that goes way over their heads.
If I were Jim Browning I would cover every single vector possible, shotgunning every possibility. Leaving executable trojans as sensitive documents on the PC, payloads in emails attachments, fake banks with downloadable “security” java plugins, a drive-by exploits at the wire transfer section of the bank account, and trojanized 2FA token generators in the banks.
Whatever sticks, sticks.
Beautiful! I was a victim of this scam about two years ago. Fortunately I got cold feet and told the scammer that I would have to talk with my wife about any expenditure over $100 and he wanted a minimum package of $350 up up up…. I told him to call me at 10 the next morning and true to form he called at exactly 10. I told him then that he was a scammer and since he had access to my computer I was disconnected and currently changing passwords and wiping all my computers and reinstalling (I have since learned that wiping was unnecessary – I could use any number of anti virus software systems).
None the less, thank you “Jim Browning” and all of you who have made the lives of these scammer “people” more difficult! I, for one, am much more cautious on line. More so now that I read how (somewhat) easy getting into my computer was!
Thanks for writing this amazing article I couldn’t find any better article than this and this also explains almost every thing any scam baiter do. It’s obvious that he cuts “THAT” part of video.
and how did you made copy paste tools to not give any search result? Do you have any article about that? of course I can look up on the internet but I like your way of explaining things.
and also that legal notice at the end ? does that means it’s illegal to scam bait?
Hi Abigail, thanks for your feedback. The technique how to disguise text but showing it anyways is an old SEO black hat technique I used to experiment with in the old days. I don’t think you’ll find anything about it in the internet. As for the disclaimer: This is a grey zone. It is not legal to hack into somebody’s computer. But if the hacker is doing it to prevent or expose a crime, then it most likely won’t be considered a crime, since the motive was not malicious. For instance, if you break into somebody’s house to expose a criminal activity, you sure won’t be charged for breaking and entering as your motive was not to gain an advantage, but to protect. A government organization however would not do this without a search warrant since they there case would be dismissed in court. But as a private person, you do not need a search warrant to expose somebody’s immoral actions. You are taking a risk of course if you were wrong. In case of hacking into a scammer’s computer — it’s quite obvious what’s going on here.
after reading this im still genuinely confused on how he does it, they honestly feel staged but i feel like it really is truly possible to dualhook the connects, with applications like anydesk, you need a special pin in order to connect to the computer, the scammer isn’t gonna LET you connect to there computer.
Big hole in your “theory”
How is the “Payload” avoiding virus detection?? Windows 10 defender won’t even let me download an INSTALLER for a keylogger…..much less run it… without having to go in and turn stuff off!
Interesting theories tho…..good effort.
Hi Ur Mom,
Thanks for your feedback. However, from a technical standpoint, there is no other way to do this. Either it’s a payload, or it’s magic. Since we do not believe in magic, it must be the payload :) There are many ways to trick Windows to accept RAT software, especially if you have programmed one and tested it yourself under Windows.
The reason why Keyloggers do not work can be explained easily. They are being released by the so-called “Release Scene” a hacker culture dedicated to race among themselves for the fastest release. They see themselves as the elite, often referred as 1337, and do not care about other users and their endeavors installing their keylogging software. That is why they do not try to accommodate with users having troubles opening it on Windows. From the Release Scene’s perspective, the keyloggers are not meant for outsiders to be used, but should only used by members of the Release Scene alone. However, if you are eager to trick Anti-Virus Software, as a skilled programmer, you will succeed.
I hope this makes sense.
Best,
William
Aye, Atsung, I had the same question. I was wondering if there was some clever way to use the open port but nope. Just a simple trojan. And there I was searching Metasploit in vain hope. When he says “reverse the connection” I was thinking of reverse HTTP payloads, etc which is effectively what this is.
What he manages to do when he gets into the network is impressive to me, but I am an amateur without the balls to go after scammers (I fear our police more than I do retaliation).
This has been insightful, i have been trying to make sense with “Jim’s” logic when he says “Reversed the Connection” and since in the video i do not see the scammer running any payload (i suppose that’s the part deleted form the video) was scratching my head on how was he able to get the payload in. Reverse Social Engineering at its best i should say.